
Securing patient data has become a challenge that requires immediate attention in the ever-evolving world of healthcare. Identifying human actions within encrypted health data without sacrificing security or accuracy is a modern medical necessity, especially when it comes to the monitoring of patient movements for elderly care, surgery recovery, or rehabilitation. An in-depth analysis of this problem will be provided, along with a look at a creative AI-powered solution and a roadmap for achieving global health equity.
Imagine a society in which sensitive health information is kept private and secure, patient data is considered inviolable, and the standard of care transcends the boundaries of conventional medicine. In the current context of digital health, this idealistic vision has become essential. Securely processing and analyzing sensitive healthcare data is the actual issue at hand, particularly when capturing and interpreting complex human skeletal joint movements. The challenge here is to recognize human actions within encrypted health data without requiring decryption while maintaining high recognition accuracy. This need can be found in a variety of scenarios, from real-time patient monitoring to rehabilitation videos.
Why does this problem matter?
Patient data security and privacy are non-negotiable in the digital age. Beyond legal requirements, it is crucial to uphold healthcare ethics, guaranteeing that each patient’s sensitive data is kept private and secure. If this issue is not resolved, healthcare facilities may be discouraged from implementing cutting-edge patient monitoring systems, which would impair both the high standard of patient care and the enormous potential for medical research.
HEAR and Homomorphic encryption
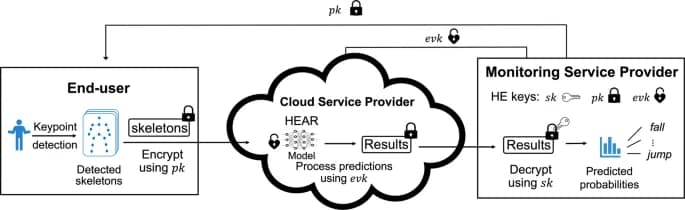
The revolutionary combination of HEAR (Human Action Recognition) and homomorphic encryption is potentially the game changer in the field of secure human recognition and patient monitoring.
- Human Action Recognition (HEAR) is a novel technique that converts intricate skeletal joint movements in humans into two-dimensional coordinates. Artificial intelligence systems can now efficiently understand and analyze these movements thanks to this simplification.
- Imagine seeing a patient’s post-knee surgery rehabilitation on video. All movements, including leg lifts and steps, are converted into simple 2D coordinates by HEAR. These coordinates are simpler for AI to comprehend and evaluate than complex graphical representations.
- Convolutional Neural Network (CNN) is the artificial intelligence system used to handle these 2D coordinates. CNNs are specific neural networks that are excellent at processing patterns and visual data. They process the simplified coordinates in the context of HEAR.
- Consider CNN as a detective with an aptitude for interpreting visual cues. In this instance, it uses the 2D coordinate “clues” to piece together the patient’s movements.
- Homomorphic encryption is, in this solution, the protector of patient data privacy. It makes it possible to process data without requiring decryption, guaranteeing the privacy of sensitive data.
- Comparable to a transparent, safe vault door is homomorphic encryption. You never have to open the door or reveal its contents to examine what’s inside. It permits data analysis in the healthcare context without disclosing personal patient information.
What makes this solution better?
One prominent application lies in rehabilitation monitoring. HEAR allows healthcare providers to securely analyze patients’ skeletal joint movements during rehabilitation exercises. Physical therapists can remotely track progress, provide personalized feedback, and ensure adherence to prescribed routines, all without compromising patient privacy.
Also, the system excels in fall detection, especially in elderly care. It can instantly recognize falls, facilitating swift assistance to prevent injuries. Importantly, it can distinguish between genuine falls and routine activities, significantly reducing false alarms that can burden healthcare resources.
In postoperative recovery, HEAR aids in monitoring patients’ movements, ensuring they follow recommended postoperative protocols. This proactive approach helps healthcare providers identify complications early, enhancing patient outcomes.
Furthermore, chronic disease management, clinical trials, telemedicine, public health surveillance, and even fitness and wellness programs can benefit from this technology. Whether it’s assessing treatment effectiveness, safeguarding clinical trial data, or enabling personalized fitness routines, HEAR and homomorphic encryption provide a secure and privacy-preserving environment for analyzing sensitive movement data.
- Sensitivity: The system’s sensitivity is its capacity to accurately detect falls when they happen. It’s comparable to the system’s ability to sound an alert when someone falls. The accuracy of the system in this instance is 86.21%.
- Specificity: The system’s ability to not sound a false alarm when someone isn’t falling is known as specificity. When it comes to distinguishing between normal activities and falsely labeling them as falls, it is 99.14% accurate.
- Speed: Every second counts in the medical field. When patients require assistance, this system can quickly respond and initiate interventions because it can make these decisions in 1.2 to 2.4 seconds.
- Comparison to other systems: It’s critical to comprehend how the ground-breaking HEAR and homomorphic encryption solution compares to its rivals, LoLa and nGraph-HE2, in our endeavor to realize secure human action recognition. Like a diligent librarian, LoLa excels at precision but can also be slow. Like a quick but occasionally lost courier, Graph-HE2 puts speed first but may occasionally sacrifice accuracy. The best of both worlds, however, is provided by HEAR and homomorphic encryption, which combine speed and accuracy to guarantee effective recognition of medical data.
Possible implementation challenges and solutions
Challenge 1: Loss of critical action data
Challenge: Data loss during preprocessing may result from an incomplete or low detection probability of skeletal joints. The recognition system might not function at its best if important action data is absent.
Solution: Using redundancy and data augmentation techniques is crucial to reducing this difficulty. To ensure that even in the event of one set being incomplete, the others can still make up for it, redundancy entails gathering multiple data points for the same action. Contrarily, data augmentation entails creating new training data artificially by transforming the current dataset in different ways, which strengthens the model’s resilience.
Challenge 2: Global adoption of homomorphic encryption
Challenge: While homomorphic encryption has great potential, it is important to put measures in place to increase its usability for global healthcare applications.
Solution: To enhance the global adoption of homomorphic encryption in healthcare, several key methods must be implemented. Firstly, user-friendly interfaces with intuitive design should be developed to simplify interaction with encrypted data, particularly in low-resource settings. Standardization and interoperability efforts are essential to ensure seamless integration with various healthcare systems. Scalable encryption solutions optimized for healthcare data are needed to reduce computational demands. Training programs, affordability initiatives, and ethical frameworks will promote understanding and acceptance. Cross-border collaboration to harmonize encryption standards can facilitate secure global healthcare partnerships. These specific methods collectively address the challenge of making homomorphic encryption a practical tool in healthcare worldwide.
Challenge 3: Adaptability
Challenge: Scaling the AI solution to benefit a broad population can be complex, especially in low-resource settings.
Solution: Putting in place a “health tech pipeline” could be the solution. This entails developing modular, flexible AI models and solutions that are simple to incorporate into the current healthcare infrastructure. The goal is to offer an organized framework that guarantees healthcare equity while enabling organizations to choose and scale solutions according to their unique needs.
The goal of safe, effective, and privacy-preserving healthcare recognition can come true by overcoming these practical obstacles and implementing customized solutions. As the world develops, it is becoming increasingly evident that compassion and technology can work together to achieve health equity.
The study demonstrates how human behavior recognition could transform patient monitoring and rehabilitation without ever requiring the decryption of private information. Are you intrigued by the potential implications of this for healthcare? Let’s explore healthcare innovations that will enhance global health equity together
Source Article: https://www.nature.com/articles/s41467-022-32168-5
Disclaimer: Please note that the opinions, content, and analysis in my posts are entirely my own and do not reflect the views of any current or past employers or institutional affiliations. These posts, based solely on publicly available information, are for informational purposes and should not be taken as professional advice. All insights and conclusions are my viewpoints and should not be considered representative of any organizations I am or have been associated with. This content is not endorsed by, nor does it represent the stance of any affiliated entity.





